Appearance
Architecture
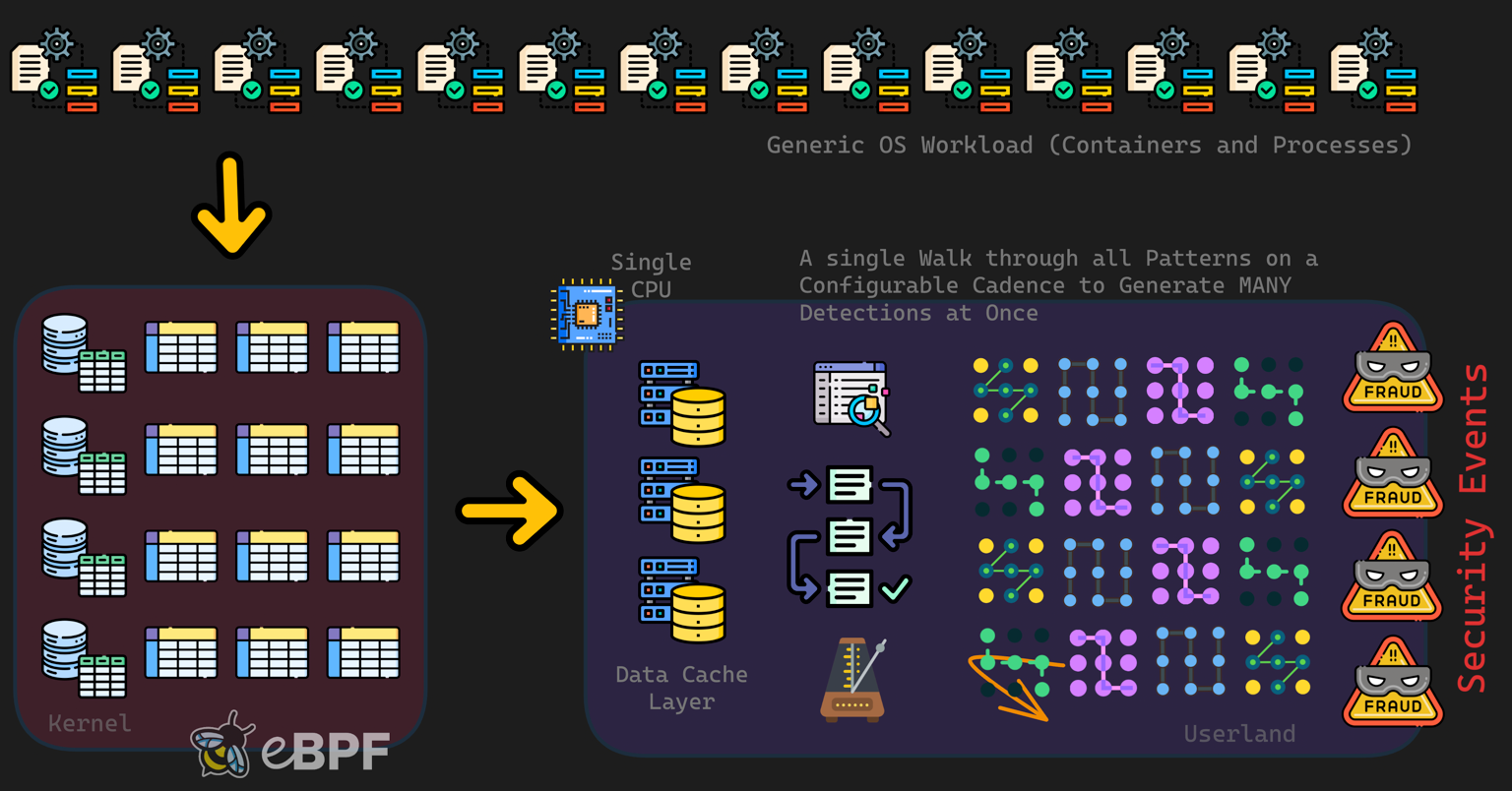
Jibril retrieves security events on demand from kernel memory rather than streaming them through ring buffers. This query-driven model eliminates overflow, bounds memory usage, and maintains constant CPU overhead regardless of event volume.
The policy enforcement happens synchronously in the kernel.
System Layers
Kernel Space
eBPF programs attach to kernel functions and store data in eBPF maps.
Event capture:
- Process execution and lifecycle
- File access and any modifications
- Network connections and DNS queries
- Container operations enrich event context
Full context of triggered event
- Process ID and name
- User context
- Execution path
- Process hierarchy
- Network connections and DNS queries
- File access and modifications
- Container operations
- and more
Storage mechanisms:
- Hash maps for event metadata and context
- Array maps for configuration and counters
- LRU maps for automatic memory management
Userspace
The Jibril runtime security agent consists of three components:
Query engine
- polls kernel maps at a configured interval,
- correlates events,
- applies filters
Detection engine
- correlations matched against detection recipes,
- events are enriched with context,
- threat scores are assigned
- AI-powered noise reduction
Output routing
- events are sent to printers
Reaction engine
JavaScript-based reactions
- process termination,
- network policy dynamic updates,
- policy enforcement for subsequent events,
- integration and alert generation.
Event data is immutable once captured, preserving forensic integrity.
Performance
| Metric | Characteristic |
|---|---|
| CPU | Constant; Low CPU overhead regardless of workload |
| Memory | Predictable; LRU eviction prevents unbounded growth |
| Latency | Predictable; Sub-second query response times |
| Scaling | Scaling does not degrade performance |
Adjust the cadences setting to trade detection latency against resource usage.
Security Properties
Kernel-level enforcement
- eBPF programs cannot be bypassed from userspace.
- root processes and container escapes remain visible.
Verified execution
- the eBPF verifier guarantees program safety before loading.
- programs run in a sandboxed environment; kernel crashes are not possible.
Complete visibility
- all processes system-wide are monitored.
- no gaps in event capture.